Most companies have invested significant capital to ensure their network and information are protected from hackers. But did you know…
Most companies have invested significant capital to ensure their network and information are protected from hackers. But did you know…
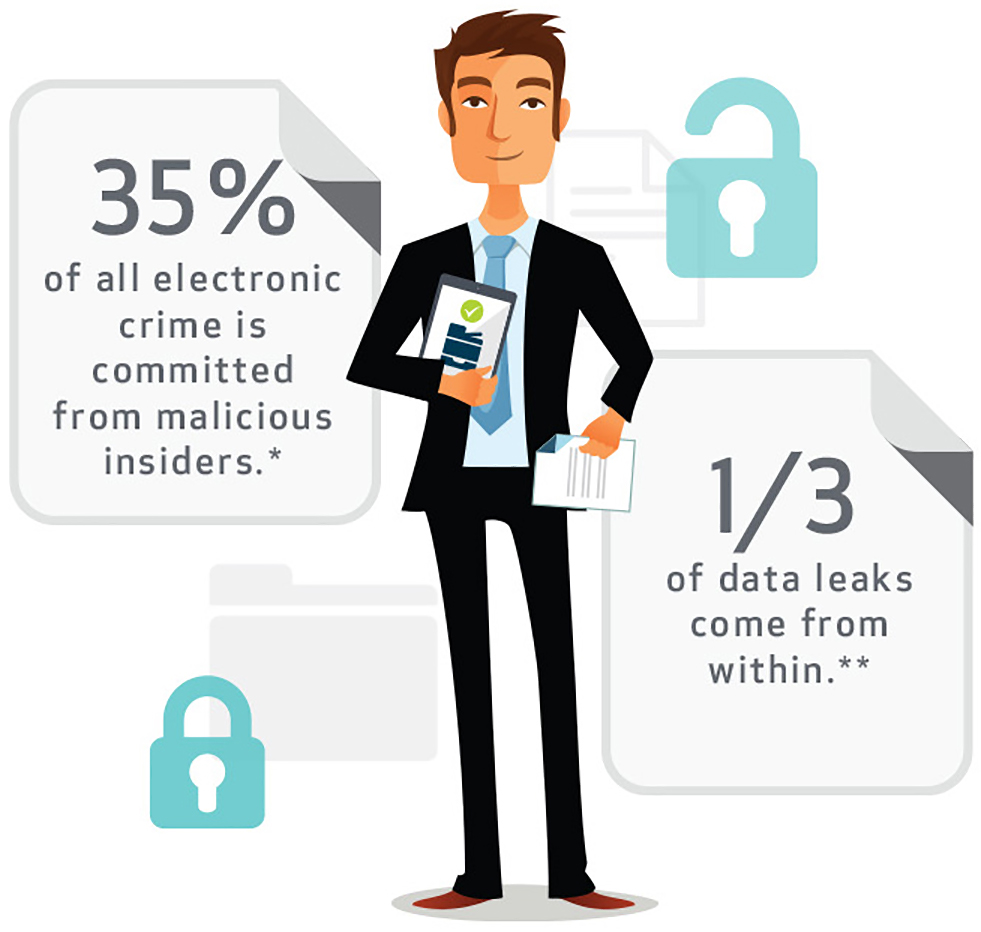
35% of all electronic crime is committed from malicious insiders.*
1/3 of data leaks come from within.**

* Source: Ponemon Institute 2015 Cost of Cyber Crime, September 2015.
** Sorce: https://blog.datalossdb.org/analysis/ (2015/Incidents by Vector-Last Year)
HELP SECURE YOUR INFORMATION
by managing these three aspects of your organization:
HELP SECURE YOUR INFORMATION
by managing these three aspects of your organization:

PEOPLE
DOCUMENTS
DEVICES + NETWORK
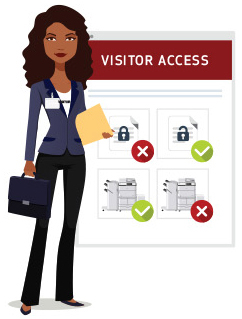
- Employees should be provided with an ID/ swipe card.
- Develop a set of permissions and access privileges that define the allowable actions of employees when printing or scanning information.
- Visiting users may access devices, but they’d have document access managed.
- Sensitive documents and information should be flagged and blocked/ restricted based on an employee’s access level.
- Use secure watermarks on corporate information.
- Data and images should be encrypted when they’re stored.
- Record fax number and e-mail destination of recipients, and consider blocking some known numbers and e-mail extensions you want to avoid.
- Consider shredding or securely disposing any documents left in recycle bins.
- Devices should be programmed to release jobs when employee is authenticated.
- Hard drives should be encrypted and routinely erased of all document content information.
- Keep a record of all print/ copy/ scan/ fax activity by user.
- Consider removing personal desktop printers that aren’t tracking documents and user access.
PEOPLE
- Employees should be provided with an ID/ swipe card.
- Develop a set of permissions and access privileges that define the allowable actions of employees when printing or scanning information.
- Visiting users may access devices, but they’d have document access managed.

DOCUMENTS
- Sensitive documents and information should be flagged and blocked/ restricted based on an employee’s access level.
- Use secure watermarks on corporate information.
- Data and images should be encrypted when they’re stored.
- Record fax number and e-mail destination of recipients, and consider blocking some known numbers and e-mail extensions you want to avoid.
- Consider shredding or securely disposing any documents left in recycle bins.

DEVICES + NETWORK
- Devices should be programmed to release jobs when employee is authenticated.
- Hard drives should be encrypted and routinely erased of all document content information.
- Keep a record of all print/ copy/ scan/ fax activity by user.
- Consider removing personal desktop printers that aren’t tracking documents and user access.
INFORM USERS
Ensure that employees understand that you have a document security plan and that information security is a priority.
INFORM USERS
Ensure that employees understand that you have a document security plan and that information security is a priority.

CANON OFFERS SOLUTIONS
that can help organization improve document security
CANON OFFERS SOLUTIONS
that can help organization improve document security




Secure Watermark
Secure watermark on selected documents.
Track Users
Track all users’ activity and restrict access and distribution of confidential documents.
Secure Print
Restrict access to devices to authenticated users/release jobs only while user is present.
HDD Erase
Erase device hardware when replacing it.

Secure Watermark
Secure watermark on selected documents.

Track Users
Track all users’ activity and restrict access and distribution of confidential documents.

Secure Print
Restrict access to devices to authenticated users/release jobs only while user is present.

HDD Erase
Erase device hardware when replacing it.
Ask your Canon representative about the various solutions available to help ensure your documents and information are protected.
Ask your Canon representative about the various solutions available to help ensure your documents and information are protected.


Canon and imageRUNNER are registered trademarks of Canon Inc. in the United States and may also be registered trademarks or trademarks in other countries. All other referenced product names and marks are trademarks of their respective owners. All images and effects are simulated. Specifications and availability subject to change without notice. Not responsible for typographical errors.
© 2020 Canon U.S.A., Inc. All Rights Reserved. Reproduction in whole or in part without permission is prohibited.